Training
Training Courses
Course Catalog
*Courses may vary.
Search Courses

Computer Security with Paige the Panda
This module for kids talks about how to use computers safely.
3:12 minutes
EAL Browser Event
This module teaches users how to browse the web safely.
2:34 minutes

Sensitive Data Exposure
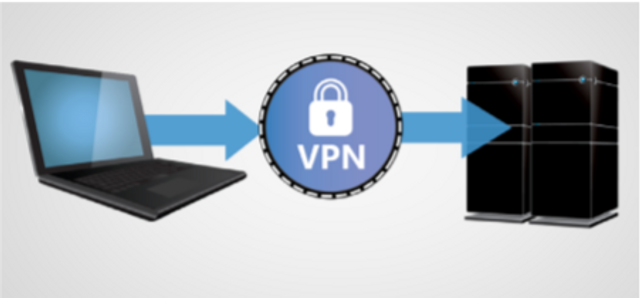
Public Networks and Computers

Spoofed Email Address

Better Together (Two Factor Authentication)
This micro-learning module explains two-factor authentication in a delicious way!
0:35 minutes

Secure Password Storage (Video)
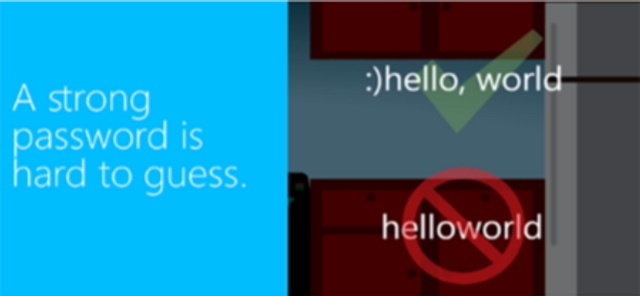
Creating Strong Passwords (Video)
This short video details the process of choosing secure, robust passphrases in under one minute.
0:46 minutes

Securing Privileged Access

Introduction to Account Takeover Attacks (ATO)
Learn about account takeover attacks: what they are, what they aim for, and how to keep yourself safe from them.
5:32 minutes
Password Security for Educators

Password Security for Financial Institutions
Our interactive Password Security module stresses the importance of following internal policies regarding access to sensitive financial information.
9:32 minutes
Password Security for Healthcare Managers
It will show healthcare managers how to pick strong passwords and keep them safe, how to securely set passwords for employees and how to help employees with password security related challenges.
10:32 minutes

Password Security for Healthcare Executives

Password Security for Healthcare Professionals and Providers
Password Security for Managers
This module will show managers how to pick strong passwords and keep them safe, how to securely set passwords for employees and how to help employees with password security related issues.
11:50 minutes

Password Security for Executives
This module will teach executives how to create strong passwords and keep them safe, and show how they can personally support secure password management policies and habits within their companies.
10:39 minutes

Phishing Assessment (Capital One) W/ Hints
This assessment module will test a learner’s ability to recognize suspicious email elements through a realistic email mimicking Capital One communications.
0:30 minutes
Phishing Assessment (LinkedIn) W/ Hints

Suspicious Hosts Assessment (Google)

Phishing Assessment (Capital One)
This assessment module will test a learner’s ability to recognize suspicious email elements through a realistic email mimicking Capital One communications.
0:30 minutes
Phishing Assessment (LinkedIn)
This advanced assessment module will test a learner’s ability to recognize suspicious email elements through a realistic email mimicking LinkedIn communications.
0:30 minutes

Breach Notification
This module details best practices for detecting and reporting unauthorized Protected Health Information (PHI) disclosures.
8:14 minutes
Recognizing Phishing Emails (Video)
This short video covers some of the common signs of phishing emails and how to recognize malicious links.
2:27 minutes

What Is Phishing? (Video)

Request your free demo today.
Please complete and submit the form below.


