Training
Training Courses
Course Catalog
*Courses may vary.
Search Courses

Physical Security and PHI

Physical Security for Executives

Data Retention
This module walks learners through common data retention plans, data types typically subject to data retention policies and secure data disposal considerations.
4:32 minutes

Data Destruction
This module reinforces the importance of secure data-disposal methods and shares best practices for disposal of sensitive data.
2:17 minutes

Software Licensing (Video)

EAL Malware
This module teaches learners how to avoid falling victim to malware.
1:46 minutes
Appropriate Use of Software (Video)
In less than 60 seconds, this module covers how to legally use products of creative software.
0:58 minutes
Intellectual Property

Intellectual Property Rights (Video)

Antivirus (Video)
This video details the threats antivirus software can and cannot mitigate.
0:47 minutes
Updates And Patches (Video)
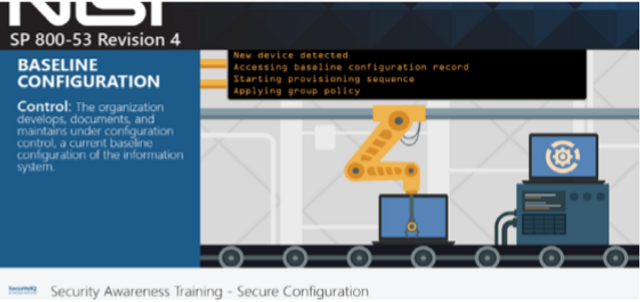
Secure Configuration
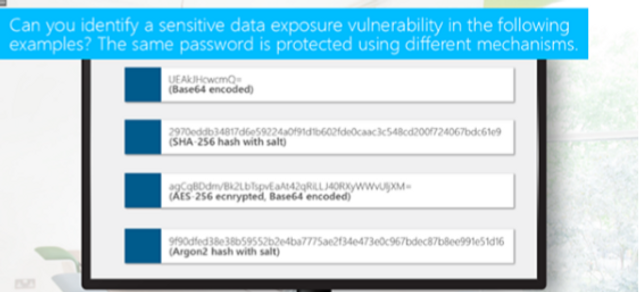
Security Misconfiguration

Using Components with Known Vulnerabilities

Vulnerability Management
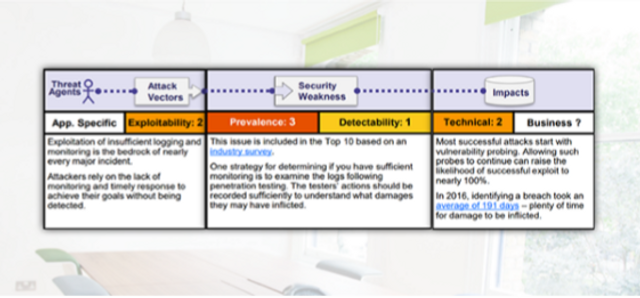
OWASP A10 - Insufficient Logging and Monitoring

OWASP A6 - Security Misconfiguration

OWASP A9 - Using Components with Known Vulnerabilities

Check (Automatic Updates)
This micro-learning module highlights the importance of enabling automatic updates.
0:35 minutes
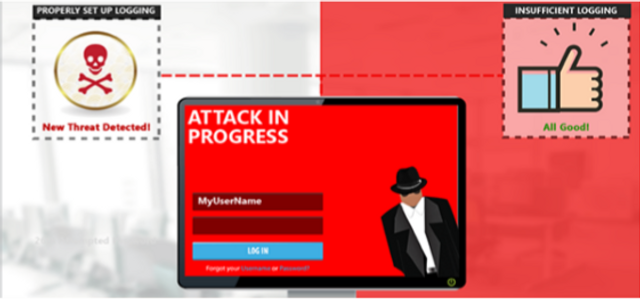
Insufficient Logging and Monitoring

Insufficient Attack Protection

Malware for Educators
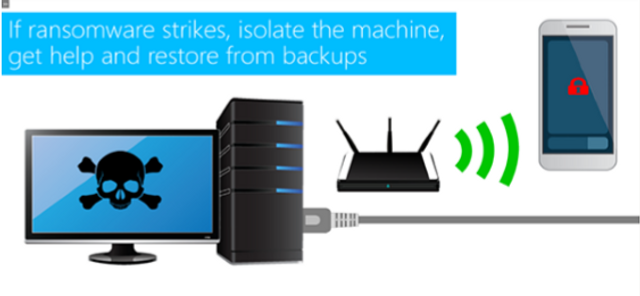
Ransomware and HIPAA

Malware for Financial Institutions

Malware and PHI for Managers

Request your free demo today.
Please complete and submit the form below.


