Training
Training Courses
Course Catalog
*Courses may vary.
Search Courses
Public Networks and Computers

Spoofed Email Address

Better Together (Two Factor Authentication)
This micro-learning module explains two-factor authentication in a delicious way!
0:35 minutes

Secure Password Storage (Video)
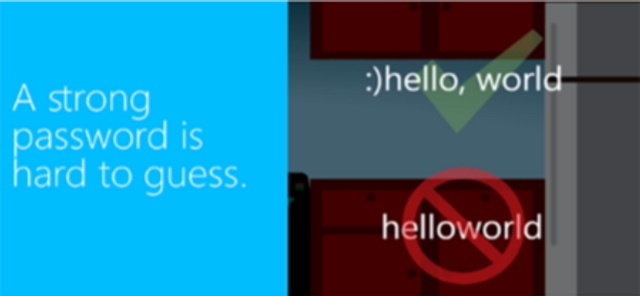
Creating Strong Passwords (Video)
This short video details the process of choosing secure, robust passphrases in under one minute.
0:46 minutes

Securing Privileged Access

Introduction to Account Takeover Attacks (ATO)
Learn about account takeover attacks: what they are, what they aim for, and how to keep yourself safe from them.
5:32 minutes
Password Security for Managers
This module will show managers how to pick strong passwords and keep them safe, how to securely set passwords for employees and how to help employees with password security related issues.
11:50 minutes

Password Security for Executives
This module will teach executives how to create strong passwords and keep them safe, and show how they can personally support secure password management policies and habits within their companies.
10:39 minutes

Phishing Assessment (Capital One) W/ Hints
This assessment module will test a learner’s ability to recognize suspicious email elements through a realistic email mimicking Capital One communications.
0:30 minutes
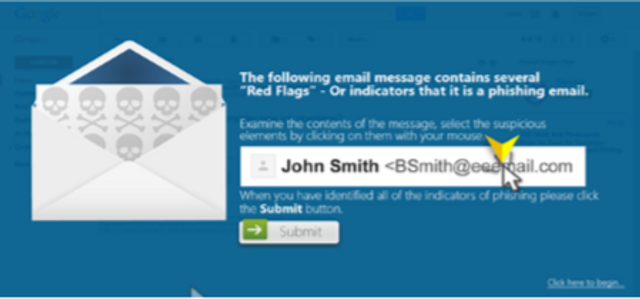
Phishing Assessment (LinkedIn) W/ Hints

Suspicious Hosts Assessment (Google)

Phishing Assessment (Capital One)
This assessment module will test a learner’s ability to recognize suspicious email elements through a realistic email mimicking Capital One communications.
0:30 minutes
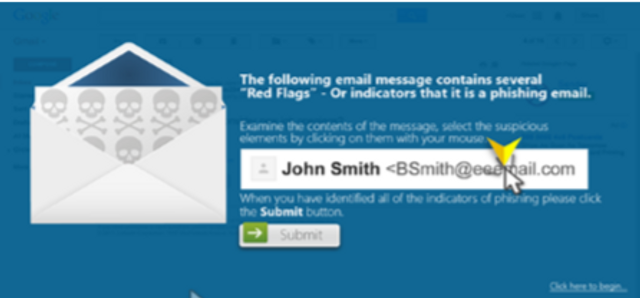
Phishing Assessment (LinkedIn)
This advanced assessment module will test a learner’s ability to recognize suspicious email elements through a realistic email mimicking LinkedIn communications.
0:30 minutes

Breach Notification
This module details best practices for detecting and reporting unauthorized Protected Health Information (PHI) disclosures.
8:14 minutes
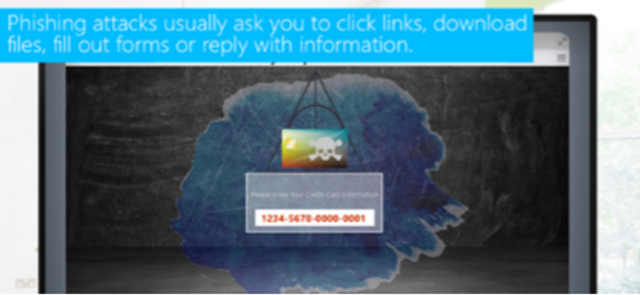
Recognizing Phishing Emails (Video)
This short video covers some of the common signs of phishing emails and how to recognize malicious links.
2:27 minutes

What Is Phishing? (Video)

EAL Phishing
This module teaches learners how to avoid falling victim to phishing.
2:11 minutes

Phishing for Executives
This module explains the risks phishing poses to executives and organizations, and suggests ways executives can work with their security teams and staff to keep information secure.
10:04 minutes
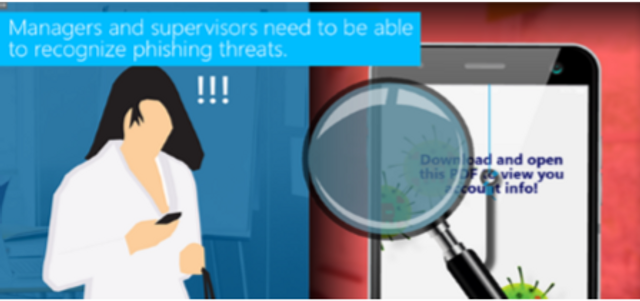
Phishing for Managers
This module discusses phishing in detail and teaches managers how to detect phishing attempts. It also outlines how managers can work with their teams to protect their company from phishing attacks.
11:02

Marine Lowlifes: Spearphish
Target sighted! Follow the hunt of that vicious but sometimes misaimed predator, the Spearphish.
1:30 minutes

Marine Lowlifes: Whaling Shark
The wonders of nature are displayed up close as the Whaling Shark chases its prey, the powerful and important Whale.
1:23 minutes

Marine Lowlifes: Common Phish
Dive into the Sea of Emails for a closer look at one of the oldest scams still swimming today: the Common Phish.
1:25 minutes

Marine Lowlifes: Clone Phish
Sink into the depths to observe the Clone Phish, which disguises itself as a previously trustworthy message to lure in prey.
1:18 minutes
Conclusion
This module will review critical lessons from your security awareness training to increase team retention of core program content.
2:05 minutes

Request your free demo today.
Please complete and submit the form below.


