Using Components with Known Vulnerabilities
This module discusses use of components with known vulnerabilities that may undermine application defenses and enable various attacks. 3:29 minutes
*Courses may vary.
Search Courses


















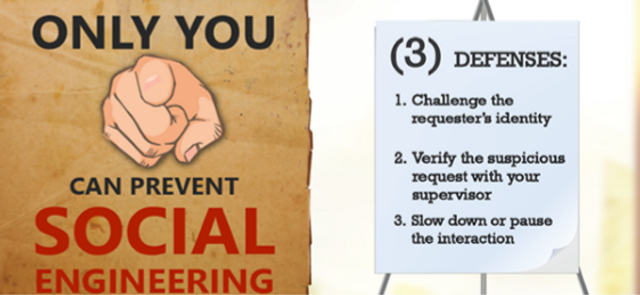

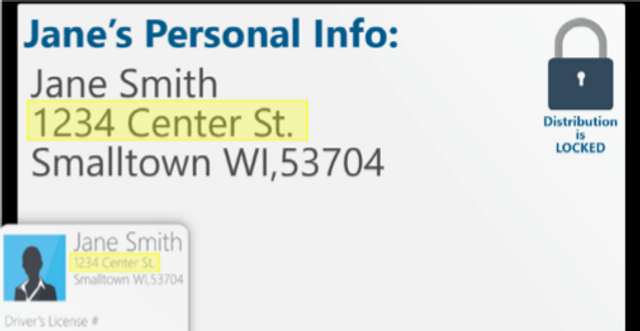



Please complete and submit the form below.

